Enterprise mobility IT security is often likened to insurance. Something you account for simply because you have to have it. However, this limited view misses the point. Security provides more than just cover in response to a specific event. It can provide assurance too – allowing your enterprise to operate and innovate without the risk of data breaches.
In this whitepaper, we explore the key considerations for developing a robust mobile security policy. We present the key risks and what you can do about them so you can set in motion new opportunities to improve productivity, efficiency, and accuracy across your operations.
No one-size-fits all approach
There remains some difference of opinion over the value of security. What everyone can agree on is that it is a complex subject that touches many areas of the organization. When you consider the variety of mobility use cases, application methodologies and deployment options of individual enterprises, the overall value of security, as well as the complexity, becomes more evident.
In a retail store, staff with tablets can serve customers quickly. But those customers want assurances that the personal information they hand over is safe on these devices. In manufacturing, there is the rise of wearable technologies to consider. This change will mean securing the flow of data from a large number of end points.
Application methodologies also vary depending on the use case and the type of device. From web-based apps through to native mobile apps or even hybrids, each instance places unique security demands on the enterprise.
The mobile deployment options available can add another level of complexity. If the enterprise encourages Bring Your Own Device (BYOD) or uses consumer-grade technology then the IT team might have to commit additional resources. They will have to develop in-house security solutions when consumer-grade mobile operating systems (OS) do not provide the required levels of security. There are also additional concerns when it comes to protecting network activity and security for WAN or WLAN connectivity.
Mobility platforms must deal with each of these security considerations at the same time as responding to the organization demand for more IT on-the-go. The goal for any enterprise should be preserving data security without disrupting day-to-day operations. So what are the core threats and what should a robust mobile security policy include?
There is the rise of wearable technologies to consider. This change will mean securing the flow of data from a large number of end points.
Identifying the risks
The basic characteristics of mobile devices mean they are exposed to a significantly higher number of security threats compared to desktops. The small and portable form factor puts them at risk of theft. Multi-purpose operating systems and applications can create multiple pathways for cyber criminals to exploit if not properly managed. Plus, communication over open and unprotected Wi-Fi or cellular connections reduces the protection of enterprise or customer data, thereby requiring additional consideration for controlling access to unsecured networks.
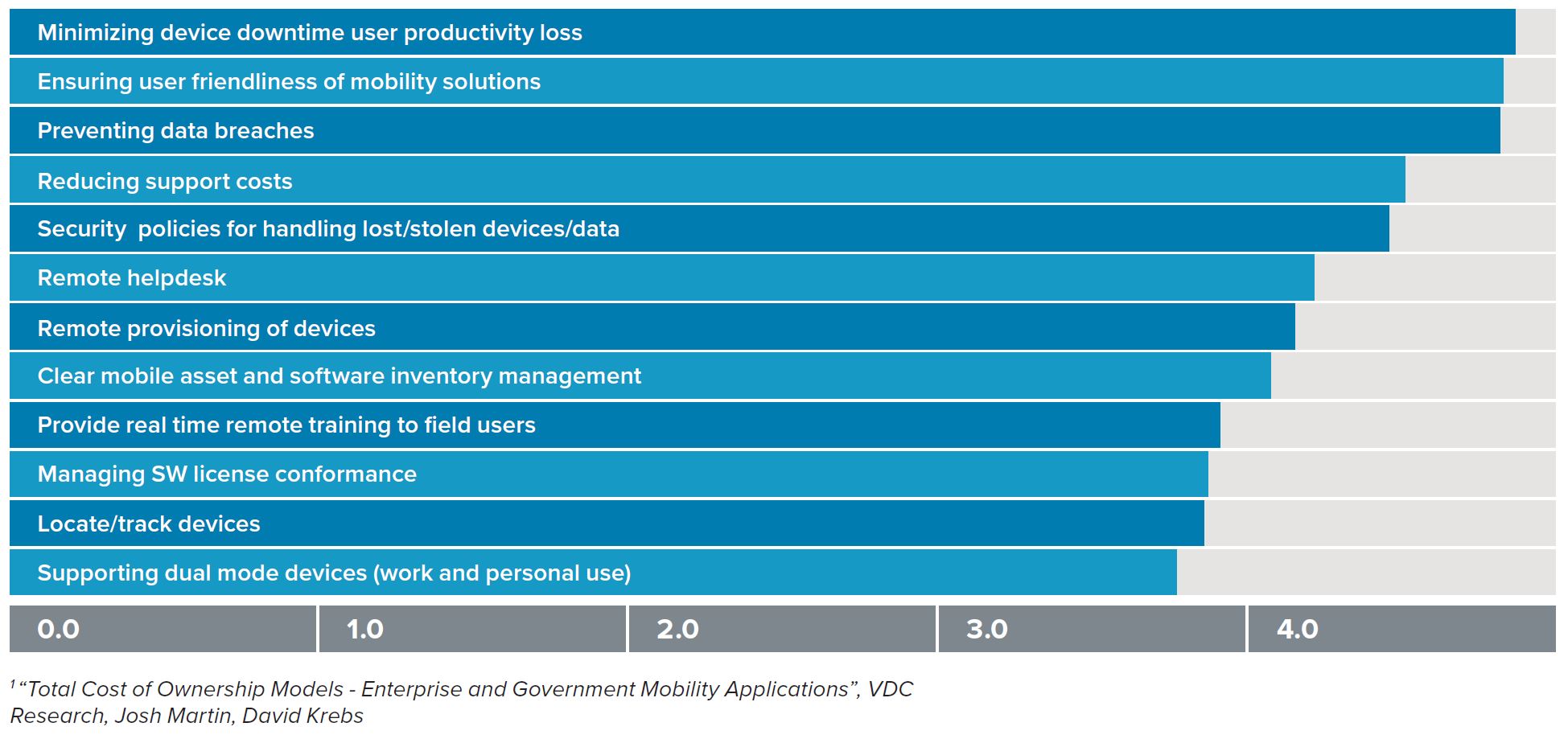
According to industry analysts VDC, preventing data breaches is one of the top three enterprise mobility investment concerns. Having security policies in place for handling lost or stolen devices and data is also in the top five – behind minimizing downtime, ensuring user friendliness, and reducing support costs.
Rate the following mobility issues in terms of their importance to your firm (1=Extremely unimportant; 6=extremely important)
These are not simplistic risks either. Drill down into the overarching security concerns and you will find both internal and external threats. The VDC research is corroborated by a TechTarget SearchSecurity survey into the top five enterprise mobile security issues. Each of the big issues identified by its 487 respondents related to concerns over corporate data.
- Device loss – e.g. leaving a corporate tablet or smartphone behind in a taxi or restaurant
- Applications security – e.g. data being made available to developers of free mobile apps
- Device data leakage – e.g. the risk of cybercriminals accessing corporate applications running on personal devices
- Malware attacks – e.g. Trojans, monitoring tools, or malicious applications
- Device theft – e.g. data exposed after a premium device has been stolen
What is at stake is the organization’s reputation and revenue. As one article on CIO.com states, “The more that employees and contractors use mobile devices to access organizational systems, applications and data, the more important it is to protect such access. Furthermore, it’s essential to prevent the mobile devices that are supposed to boost productivity and add to the bottom line from opening unauthorized means of access to information and other assets; this turns them into a danger and a possible drain on revenue instead.”
The question remains: What specific action can your organization take to deal with the ongoing threat of enterprise mobile security issues?
Combatting the threat
With an increasing reliance on mobile technologies, enterprises must look for a more fluid response to security issues. An aggregation of analysis by Gartner, Forrester, and Information Week shows just some of the key responses that IT teams can take to deal with internal and external risks.
Forrester also advocates the following seven responses as key for mobile device management (MDM) and mobile security:
- PIN enforcement (strong passwords)
- Selective wipe (essential for a BYOD program)
- Jailbreak/root detection
- Data encryption
- Virtual private networks (VPN)
- Data leak protection (preventing authorized users from carelessly or maliciously leaking data)
- ActiveSync device restriction
Both sets of measures are effectively only ‘wishlists’ from IT if the enterprise is not willing to take mobile security seriously. Executives play a key role in elevating security to the boardroom and committing resources to combatting increasingly sophisticated threats.
To do this effectively, it pays to understand the most common regulatory requirements and international best practice for security. A brief review of these standards highlights the measures that every enterprise should be including in their mobile security policy:
- Protecting against lost or stolen devices
- Protecting data-in-motion
- Protecting data-at-rest
- Mobile Application Management
- Ensuring regulatory compliance
- Device control, admin, and monitoring
- High level data-privacy protection
- Minimizing admin costs to maintain secure platforms
- Providing strong authentication/access controls
- Maximizing use of legacy IT infrastructure
The enterprise must then move forward with a mobile policy that includes these security measures at its core. Alongside use case scenarios, security should be just as influential in the choice of devices and operating system.
The cost of making the wrong mobility choices
Given the proliferation of security risks, enterprises lured by low-entry prices must re-evaluate the use of off-the-shelf, consumer-grade devices. Most consumer grade operating systems on these devices do not come with all the security features enterprises require. Studies show that the total cost of ownership (TCO) of using consumer-grade devices for enterprise applications can be between 40% and 78% higher than purpose-built enterprise devices. Security is an important element in this differential.
Consumer devices used in enterprise applications are often an invitation to a security breach. In one BYOD study by Decisive Analytics, nearly half (46.5%) of the companies surveyed reported a data or security breach as a result of an employee-owned device accessing the corporate network. Significant investments are being made to counter this threat. However, there are no guarantees that these security workarounds will continue to be effective against emerging threats.
In contrast, purpose-built rugged enterprise devices are designed and augmented to satisfy and simplify compliance with key regulatory mandates on security. The scope of security compliance can range from the very broad (e.g. user training) to the very detailed (e.g. validation of the integrity of cryptographic algorithms).
No device or mobile OS platform can independently assure compliance. But obtaining devices and software platforms from a manufacturer that focuses on security mandates will increase the likelihood of compliance and reduce the administrative burden of validation. In turn, this reduces the cost of audits, may prevent monetary fines/penalties, and may eliminate the need to report a data breach. All of which add up to improving the bottom line.
“277 million mobile devices to run some kind of protection by 2016.”

Spotlight on OS and app security: Android
Enterprises looking at consumer-grade devices have a choice of several key market players: Google, Apple and Microsoft. Google’s Android platform has the dominant market share (81% of global market in 2015)5. Its intrinsic security offering also makes it attractive to enterprises considering consumer-grade devices. Especially when compared to alternative consumer mobile OS platforms. Application sandboxing, resource access permissioning, and data encryption are just some examples of the strong security features of Android.
Most concerns with Android security originate with potential malware within GooglePlay – the platform’s app store. Apple tightly screens its AppStore apps because it retains strict control over the signing process. Despite this, the security risk with GooglePlay is one that extends to all public app stores. Each is vulnerable to malware and privacy invasion (even Apple’s AppStore).
The best practice for running ‘Corporate Liable Devices’ is to provide application lockdown and/or use a trusted enterprise app store. Zebra’s Mobility Extensions (Mx) offers increased protection. By simplifying compliance to mobility requirements and regulatory demands, organizations can experience enterprise-grade security on consumer-grade devices.
Allied with an enterprise app store, extensions that include white listing, AD/LDAP authentication, key management and other core enterprise security functionality, will ensure IT teams can issue consumer-grade devices with confidence.
What is clear is that mobile security is about more than just insuring the integrity of the enterprise in the event that data and devices are breached. It can support operational requirements specific to the overall mobile strategy and reduce total cost of ownership across enterprise mobility rollouts. Foremost, mobile security will continue to be evolutionary and will require vigilant, continual review and updates.
While enterprise mobility has come a long way in just a few short years, the complexity of the security landscape has changed (and continues to change) beyond recognition. The challenges are complex and the solutions wide-ranging. They should be explored individually and alongside the organisation's priorities. There is no point having a stringent security policy if it restricts your operations and makes you uncompetitive and your workers unproductive. On the other hand, focusing on everything but security will leave you open to attack. The most robust mobile security policies will mitigate the risks you face while leaving you free to operate and innovate.
The key is to balance priorities within your mobile security policy – accommodating your key business requirements and end user needs with security sub-policies that match different use cases.
A useful checklist
Given the complexity and number of key considerations, developing your workforce mobile security policy can appear to be a difficult task. This checklist should help you ensure that whatever choices you do make are successful across your organization – particularly, in balancing user, enterprise, and security requirements.
- Educate everyone
Make sure everybody’s aware of security threats and create clear usage policies that explain what’s expected.
- Change passwords regularly
It’s best practice to update passwords at least every 30 days, and you should consider building mandatory password changes (with password strength criteria) into your applications.
- Get complete visibility of all your devices
Use mobile device management tools to immediately locate lost or stolen devices and kill the device or wipe data. And use monitoring and alerts to know where every device is and how it’s being used.
- Create a whitelist
Ensure people access only a whitelist of websites – those that you approve for use with your devices.
- Protect against malware
By whitelisting internal apps and application sources on your devices you can protect against vectors of infection. Additionally, controlling the device’s ability to ‘side-load’ external applications – either via an external connection or from a storage card – is a critical consideration to guard against malware and other nefarious applications.
- Update your devices
Ensure your devices are always running the latest software, with controlled and/or automated updates.
- Containerize your data
Configure your devices so that data is containerized in separate encrypted areas, making it virtually impossible for attackers to access the data.
- Deploy full encryption
Where people are working with highly sensitive data, you can encrypt your data stored on devices, as well as any data sent over wireless networks.
- Use an enterprise app store
Access to public app stores should be avoided and applications should be downloaded from a trusted enterprise app store.
- Constantly reassess security
Mobile security isn’t a fire-and-forget exercise – it’s vital to continually update your strategies and best practices to handle constantly evolving threats
SEE WHY SECURITY IS JUST THE START WHEN CHOOSING A NEW MOBILE OS. EXPLORE THE OTHER KEY CONSIDERATIONS AT WWW.ZEBRA.COM/MOBILITYREVOLUTION